# FreeNAS
# Changing the Active Directory account used by FreeNAS
If you try to change the account name that FreeNAS uses to connect to Active Directory, it will probably give you a weird error that doesn't make any sense.
You'll need to modify the file at /etc/directoryservice/ActiveDirectory/config
There will be an entry for ad_bindname= and ad_binddn=. Change these accordingly.
# Wiping Active Directory settings from FreeNAS
Ensure that all AD/SMB services have been stopped
Rename/delete the file at
/etc/directoryservice/ActiveDirectory/configDelete the settings from the sqlite db
Connect to the database filesqlite3 /data/freenas-v1.dbTurn on headers so you can see what the column names are
.headers onCheck that your settings are in this table
> SELECT * FROM directoryservice_activedirectory;Delete the settings from the
directoryservice_activedirectorytable> DELETE FROM directoryservice_activedirectory WHERE id = 1;Delete/Rename
*.tdbfiles from/var/db/system/samba4
# Rejoin Domain
If FreeNAS won't rejoin the domain after a computer name change, try Wiping AD first, re-add your settings in the UI and then run:
net ads join -U Administrator
You should be able to use any Admin account in place of Administrator
# Wiping ZFS metadata
Disks that have been used in a ZFS raid will have metadata stored at the end of the disk
You'll need to enable debug flags to run the dd commands
sysctl kern.geom.debugflags=16
The example below uses sh to loop through disks da0 through da15 and zeroes the metadata at the end of the disk.
You may also need to zero the beginning of the disk in some cases.
sh
for i in `seq 0 15`; do dd if=/dev/zero of=/dev/da$i bs=1m oseek=`diskinfo da$i | awk '{print int($3 / (1024*1024)) - 5;}'`; done
Use this for a single disk, replace <DISK> with the disk that you want to wipe.
dd if=/dev/zero of=/dev/<DISK> bs=1m oseek=`diskinfo <DISK> | awk '{print int($3 / (1024*1024)) - 5;}'`
# Firewall
Freenas doesn't come with an interface for creating firewall rules, this will need to be done by hand.
# Create the rules
Create a firewall rules file, mine is named firewall.rules.
This file will need to be stored on one of your zpools so that it does not get lost in an update/upgrade.
The rules are numbered from 1-65535, but 65535 is reserved, so you can use 1-65534.
The simplified format for the rules is: <Rule Number> <Allow/Deny> <Protocol> from <Lookup Table/Address> to <Lookup Table/Address> [dst-port <Port Number/Port Name>] [Options]
Available protocols found in /etc/protocols
Available port names found in /etc/services
Reference man page (opens new window)
#!/bin/sh
# Flush all rules before we begin.
ipfw -q -f flush
cmd="ipfw -q add "
# allow all for localhost
$cmd 10 allow ip from any to any via lo0
# checks stateful rules. If marked as "keep-state" the packet has
# already passed through filters and is "OK" without futher
# rule matching
$cmd 100 check-state
$cmd 101 allow tcp from any to any established
# Allow outgoing traffic
$cmd 102 allow all from any to any out keep-state
# Allow pings, because why not?
$cmd 103 allow icmp from any to any
# Allow SSH
$cmd 110 allow tcp from 192.168.0.0/24 to me dst-port 22
# Allow SNMP
$cmd 200 allow udp from 192.168.10.200 to me dst-port 161
# Allow web UI
$cmd 410 allow tcp from 192.168.0.0/24 to me dst-port 80
$cmd 420 allow tcp from 192.168.0.0/24 to me dst-port 443
# Allow CIFS
$cmd 500 allow tcp from any to me dst-port 445
$cmd 501 allow udp from any to me dst-port 445
$cmd 505 allow tcp from any to me dst-port 139
$cmd 506 allow udp from any to me dst-port 137
$cmd 507 allow udp from any to me dst-port 138
# Explicitly block services
$cmd 60000 deny tcp from any to me dst-port 22
$cmd 60010 deny tcp from any to me dst-port 80
$cmd 60020 deny tcp from any to me dst-port 443
# You can change this to deny instead of allow if you want to block by default.
$cmd 65530 allow ip from any to any
# ipfw built-in default, don't uncomment
# $cmd 65535 deny ip from any to any
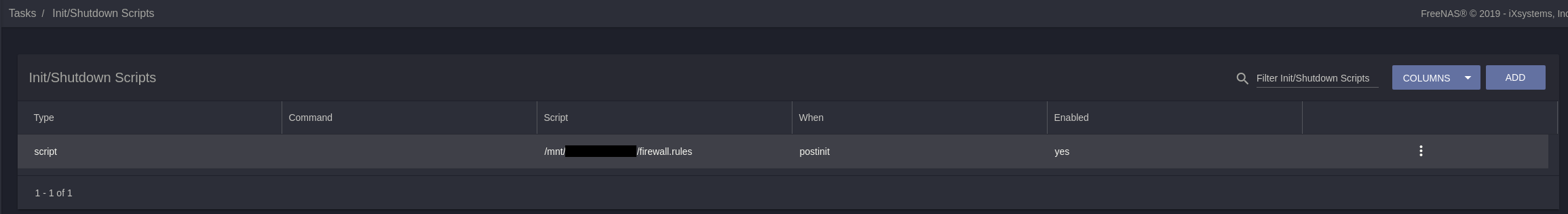
# Add startup script
You'll need to tell FreeNAS to add these rules every time it reboots.
- From the Web GUI, navigate to
Tasks>Init/Shtudown Scripts - Click Add at the top right
- Change the
TypetoScript - Locate your
firewall.rulesfile and then select it - Change
WhentoPost Init - Make sure the
Enabledbox is checked - Click
SAVE